Introduction
In today’s digital era, the use of cloud services for file storage and transfer has become commonplace for enterprises looking to boost productivity and collaboration. However, this shift to the cloud comes with its set of challenges, particularly in the realm of security. This blog post explores the risks associated with cloud-based file transfer and discusses strategies that enterprises can employ to mitigate these risks, culminating with a look at BLAZE Transfer, an end-to-end encrypted (E2EE) file transfer platform designed to secure enterprise data.
The Risks of Cloud Secure File Transfer
1. Data Breaches: One of the most critical risks in cloud file transfers is data breaches. Unauthorized access to sensitive data can lead to substantial financial losses and damage to an organization’s reputation.
2. Compliance Violations: Enterprises are often subject to regulatory requirements regarding data privacy and security. Failure to comply can result in hefty fines and legal penalties.
3. Insider Threats: Not all security threats come from outside the organization. Employees can inadvertently or maliciously expose sensitive information.
4. Insecure APIs: Cloud services are accessed through APIs, which, if not properly secured, can be a gateway for hackers to exploit.
5. Data Loss: Improper data handling and transfer protocols can lead to data being lost, corrupted, or rendered unrecoverable.

Strategies to Mitigate These Risks
1. Comprehensive Security Policy: Implementing a robust security policy that covers all aspects of data handling and file transfer is crucial. This includes clear guidelines on who can access data and under what circumstances.
2. Employee Training: Regular training on security best practices and the latest cyber threats can help minimize risks from insider threats.
3. Use of Advanced Encryption: Data should be encrypted both at rest and in transit. Enterprises should ensure they use strong encryption protocols to protect data integrity and confidentiality.
4. Regular Audits and Compliance Checks: Regularly auditing security practices and compliance can help enterprises stay on top of potential vulnerabilities and ensure they meet regulatory requirements.
5. Multi-factor Authentication (MFA): Implementing MFA can add an extra layer of security by requiring additional verification methods to access sensitive information.
Shift to a Secure file transfer
In 2022, nearly half of businesses identified more than 40% of their cloud-stored data as sensitive. By the following year, this percentage had escalated to 75%. Despite this significant amount of sensitive data, an industry report indicates that less than 50% of the typical data stored in the cloud is encrypted.
As cyberattacks on cloud services continue to rise, it becomes increasingly important for businesses to prioritize secure file transfer protocols.
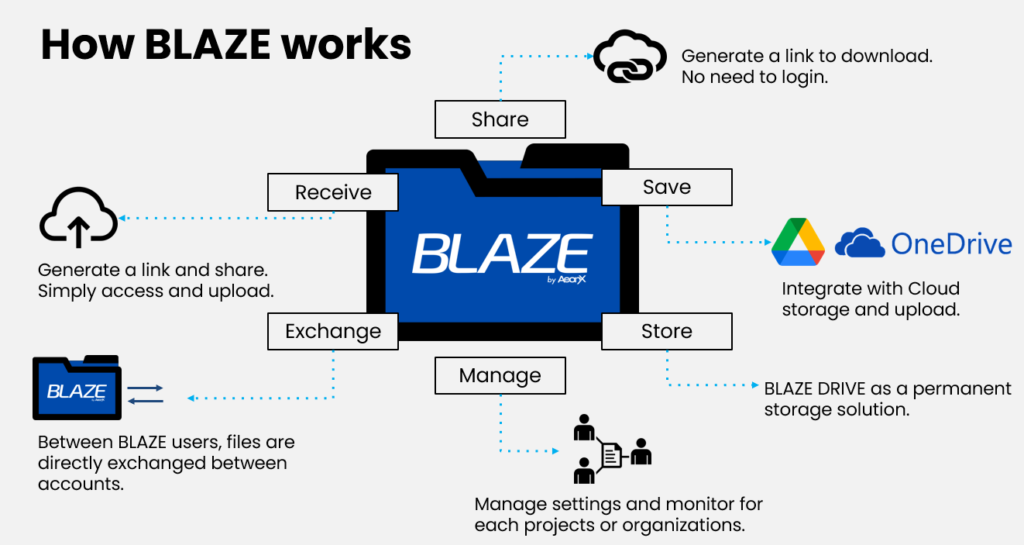
As businesses increasingly prioritize robust security frameworks, BLAZE Transfer stands out as a top-tier solution tailored for secure enterprise file transfers. This platform is engineered to facilitate the secure exchange of data through end-to-end encryption (E2EE), ensuring that files can only be read by the sender and the intended receiver.
Conclusion
The shift towards cloud-based file transfer solutions brings several security challenges for enterprises. However, adopting solutions like BLAZE Transfer can greatly mitigate these risks. By prioritizing state-of-the-art encryption and adherence to security protocols, BLAZE Transfer offers a secure and efficient method for enterprises to handle their file transfer requirements without sacrificing security.
For enterprises aiming to secure their digital assets in the cloud, integrating a platform like BLAZE Transfer into their operational framework is a strategic move to shield against the dynamic nature of cyber threats.







